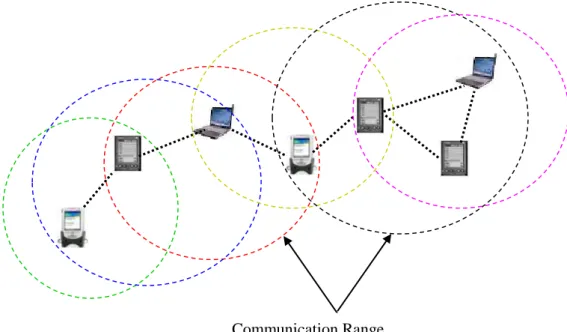
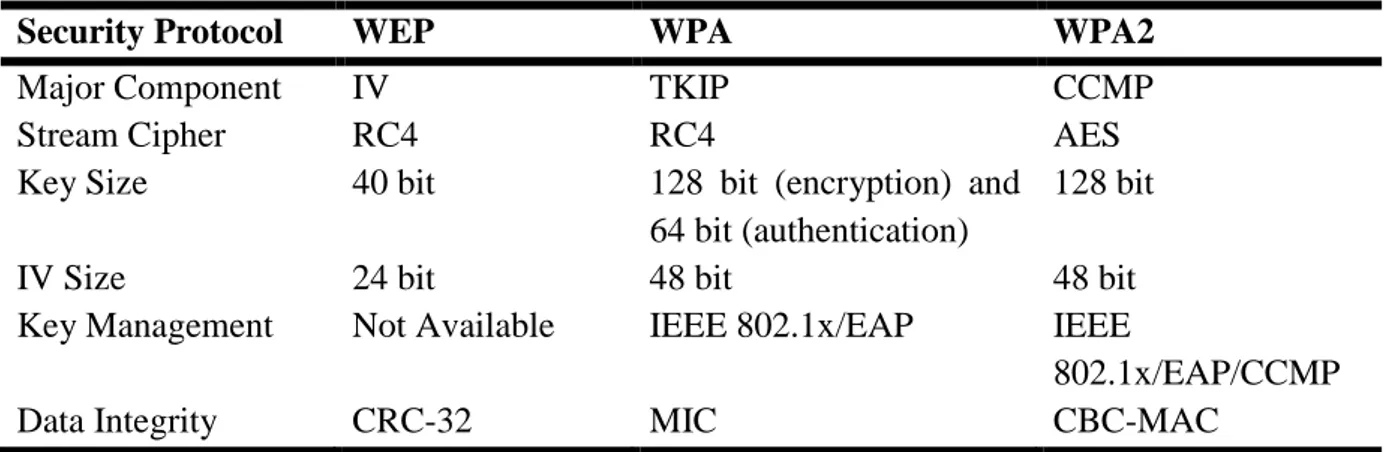
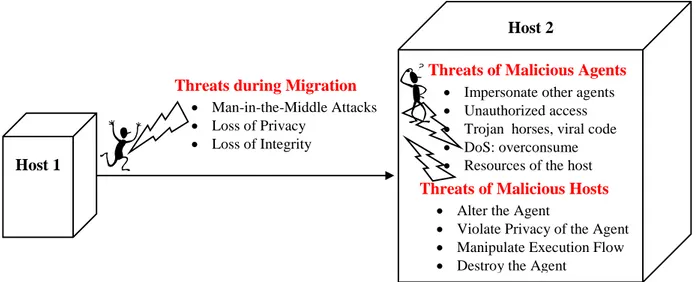
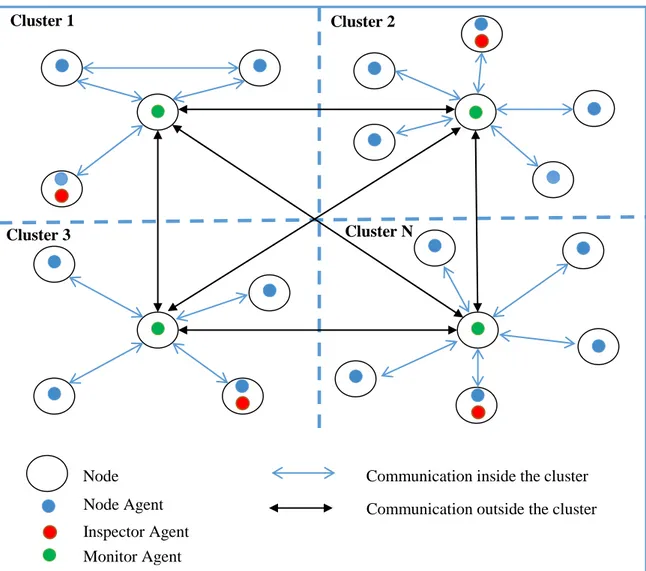
Sécurité Basée Agent Mobile Dans Les Réseaux Sans Fils
Texte intégral
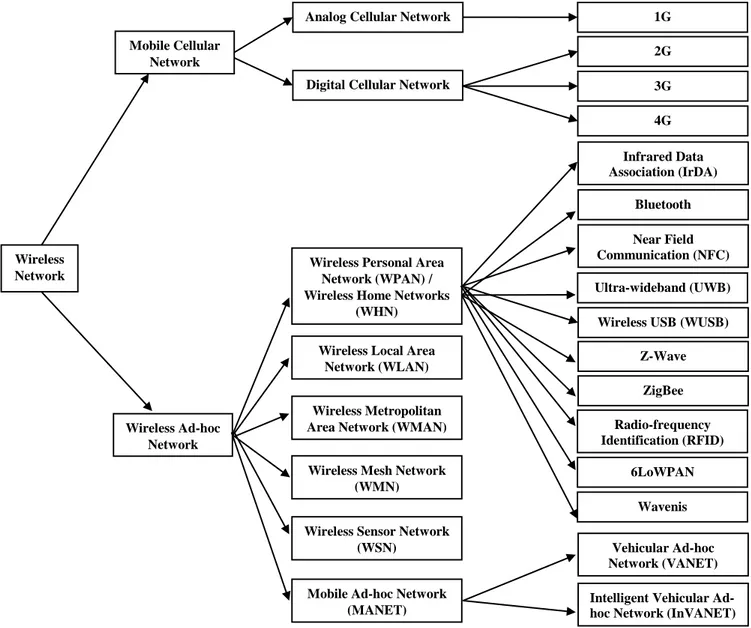
Figure
![Figure 2.2: Illustration of WLAN Configuration: (a) ESS Composed of Infrastructure BSS, and (b) IBSS [28]](https://thumb-eu.123doks.com/thumbv2/123doknet/2186662.10945/31.892.129.788.803.1093/figure-illustration-wlan-configuration-ess-composed-infrastructure-ibss.webp)
![Figure 2.3: Components of a Wireless WAN [35]](https://thumb-eu.123doks.com/thumbv2/123doknet/2186662.10945/33.892.141.793.810.1098/figure-components-wireless-wan.webp)

Documents relatifs
We mainly focus on the existence of a solution to the problem, in presence of passive or active attackers. To do so, we use a binary notion or trust: a node does trust another node,
Quality of service forest (QoS-F) is a distributed algorithm to construct a forest of high quality links (or nodes) from net- work point of view, and use these for routing
The observational congruence allows us to verify whether two networks exhibit the same observable probabilistic behaviour (connectivity), while the preorder is used to compare
We use the combination of fully self-organized security for trust model like PGP adapted to ad-hoc technology and the cluster- ing algorithm which is based on the use of trust
To achieve this goal, a robust DDM Z should be created by selecting the best RA nodes based on nodes’ selection criteria function and according to nodes location.. This will
That opacity creates major risks since bias (for instance data not updated, partial or irrelevant) and error programming are consciously or unconsciously possible. Beyond that, our
The main contributions of this work are in the analysis of basis for identification of suitable high-level information security metrics for mobile ad hoc networks and in the
However it is possible to compute probability density function of the nodes moving according to random waypoint mobility model within an environment closed, bounded, limited and