Linear algebra algorithms for cryptography
Texte intégral
Figure


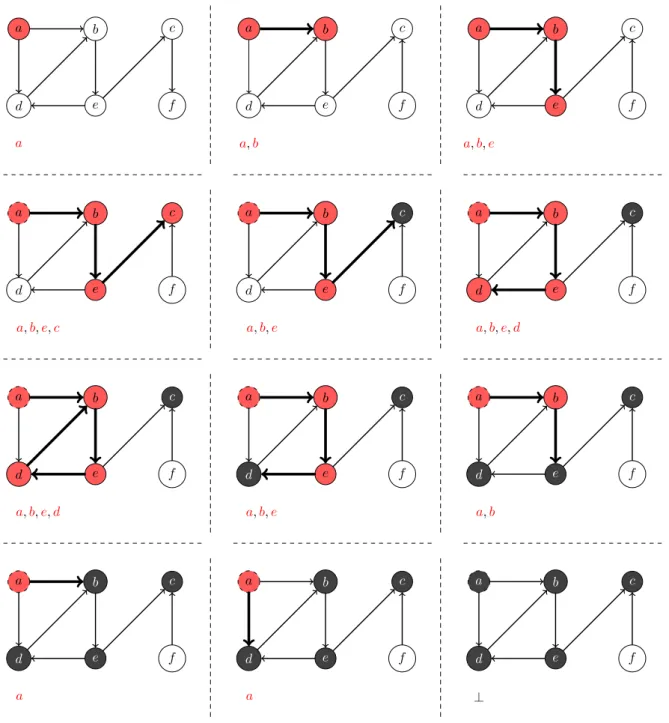
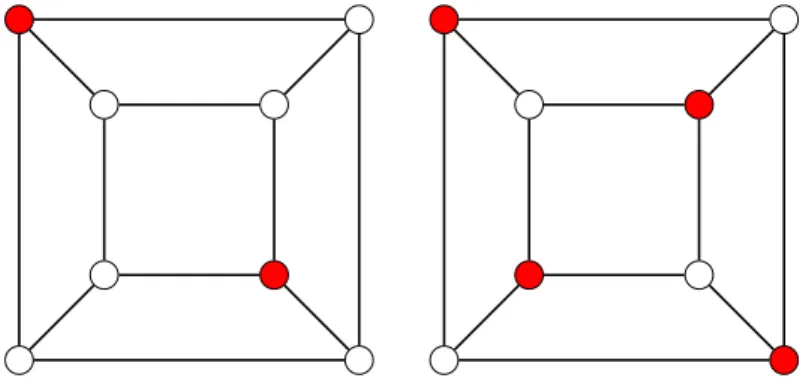
Documents relatifs
As with the field type, we need a common object interface to describe how algorithms are to access black box matrices, but it only requires functions to access the matrix’s
20 - Toutes les informations de cette page sont incroyables
L’archive ouverte pluridisciplinaire HAL, est destinée au dépôt et à la diffusion de documents scientifiques de niveau recherche, publiés ou non, émanant des
To verify the floating-point solution of a linear system, we adapt floating-point iterative refinements to interval arithmetic [NR]. By using alternately floating-point and
Considering that state of the art in metric learning, be it for feature vectors or time series, is oriented towards the k-NN classifier, it would be a major result to
We then apply the new variable-time amplitude amplification to design the quantum algorithms for solving systems of linear equations and testing singularity.. We expect that
Our main idea holds for general triangular families of polynomials, but it is only for the special case of divided difference that it will lead to an efficient algorithm (see
Back to the fact that V is the initial R-linear induction algebra, we show here how to define linear maps by primitive recursion in a way similar to the usual clone of

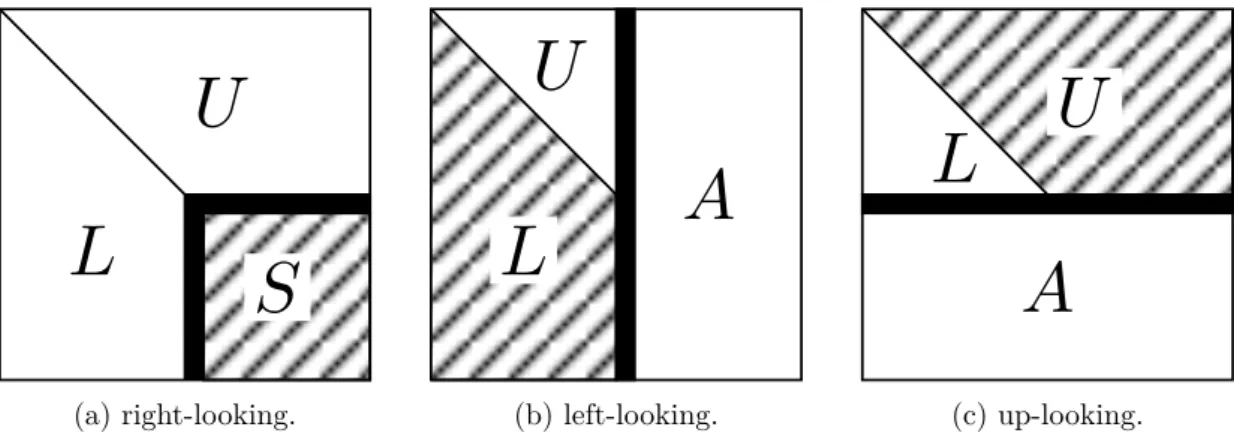

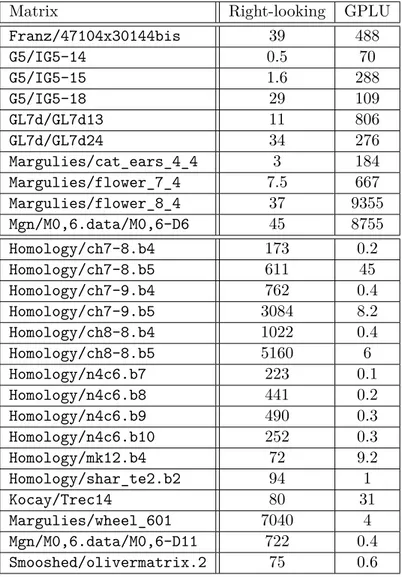
![Figure 4.2 – Example of a Gröbner Basis matrix: Grobner/c8_mat11 from [Dum12].](https://thumb-eu.123doks.com/thumbv2/123doknet/11534869.295581/57.892.262.604.368.634/figure-example-gröbner-basis-matrix-grobner-mat-dum.webp)
