Democratic and Popular Republic of Algeria Ministry of Higher Education and Scientific Research
University Ahmed Draia - Adrar Faculty of Sciences and Technology
Department of Mathematics and Computer Science
A Thesis Presented to Fulfill the Partial Requirement for Master’s Degree in Computer
Science
Option: Intelligent Systems
Title
Intrusion Detection System Based on Sensed
Relay Forwarded Packets in Wireless Sensor
Networks
Prepared by
Mrs. Ismene Laguel
Supervised by
Dr. Mohammed Omari
Academic Year 2017/2018
2
Abstract
Wireless sensor networks (WSNs) have become an optimal solution in many fields for their efficiency. Due to their vulnerability, they are usually targeted by many attacks aiming to harm their well-functioning. This work proposes an intrusion detection system that detects blackhole attackers in a WSN. A blackhole attack is an unconditional packet dropping in the network. It presents a serious problem that paralyzes the routing process. Our IDS compares forwarding ratios between nodes in order to sort out those having abnormal behavior from those with normal activity. Simulation results showed that our IDS can have up to 90% of true positive rate and an acceptable false positive rate under 2%.
Résumé
Les réseaux de capteurs sans fil (RCSFs) sont devenus une solution optimale dans pas mal d’applications pour leur efficacité. A cause de leur vulnérabilité, ils sont souvent ciblés par plusieurs attaques ayant pour intention de nuire à leur bon fonctionnement. Ce travail propose un système de détection d’intrusion qui détecte les attaquants de type blackhole. L’attaque blackhole élimine inconditionnellement les paquets du réseau et peut présenter un sérieux problème qui paralyse le routage. Notre système de détection compare les taux de transfert de paquets entre les nœuds pour distinguer ceux qui ont un comportement normal de ceux qui ne l’ont pas. Les résultats de simulation ont montré que notre système pouvait atteindre 90% de taux de vrais positifs avec un acceptable taux de faux positifs qui ne dépasse pas les 2%.
3
Acknowledgement
I would like to express my thanks to my supervisor Dr Omari
Mohamed for his patience and guidance. I’m grateful to my family for the
moral support.
4
TABLE OF CONTENTS
GENERAL INTRODUCTION ... 7
I CHAPTERI ... 8
I.1 Introduction ... 9
I.2 Sensing and sensors ... 9
I.3 Wireless Sensor Networks (WSNs) ... 11
I.4 WSNs Structure ... 11
I.5 WSNs Architecture ... 14
I.6 Challenges and Constraints ... 15
I.6.1 Energy ... 15
I.6.2 Self-Management ... 15
I.6.3 Wireless Networking ... 15
I.6.4 Decentralized Management ... 16
I.6.5 Design Constraints ... 16
I.6.6 Security ... 16
I.6.7 Other Challenges... 17
I.7 WSNs Applications ... 18
I.7.1 Military applications ... 18
I.7.2 Environmental applications ... 18
I.7.3 Health applications ... 18
I.7.4 Home applications ... 18
I.7.5 Commercial applications ... 18
I.8 Routing in WSN ... 19
I.8.1 Types of routing protocols ... 19
I.8.2 LEACH protocol and variants... 20
I.8.3 Discussion ... 25
I.9 Security in WSNs ... 26
I.9.1 Attacks model ... 27
I.9.2 Attacks Impact on nodes... 27
I.9.3 Common attacks in WSN ... 30
I.10 Conclusion ... 31
II CHAPTER II ... 32
II.1 Introduction ... 33
II.2 IDS Definition ... 33
II.3 IDS Classification ... 33
II.3.1 Anomaly based IDSs ... 34
II.3.1.1 Statistical detection based IDSs ... 34
II.3.1.2 Machine Learning detection based IDSs ... 36
5
II.3.3 Specification based IDSs ... 40
II.3.4 Discussion ... 43
II.4 Packet dropping IDSs ... 44
II.5 Conclusion ... 45
III CHAPTER III ... 46
III.1 Introduction ... 47
III.2 Proposed IDS ... 47
III.3 Implementation Environment ... 52
III.4 IDS implementation ... 53
III.5 IDS simulation and evaluation ... 53
III.6 Impact of density, random packet loss on the true positive rate ... 54
III.7 Impact of density, random packet loss on the false positive rate ... 55
III.8 Impact of density, random packet on precision, recall and accuracy ... 56
III.9 Impact of density, uniform packet loss on the true positive rate ... 57
III.10 Impact of density, uniform packet loss on the false positive rate ... 58
III.11 Impact of density, uniform packet loss on precision, recall and accuracy ... 59
III.12 Impact of uniform packet loss on the true positive rate ... 61
III.13 Impact of uniform packet loss on the false positive rate ... 62
III.14 Impact of uniform packet loss on precision, recall and accuracy ... 62
III.15 Impact of number of chances on false positive rate ... 63
III.16 Parameters selection for a better performance ... 64
III.17 Discussion ... 66
III.18 Conclusion ... 67
GENERAL CONCLUSION ... 68
6
FIGURES LIST
FIGURE 1 ARCHITECTURE OF A SENSOR NODE. ... 11
FIGURE 2 ELEMENTS OF A WSN. ... 12
FIGURE 3 COMMON STRUCTURE OF A WSN. ... 13
FIGURE 4 ARCHITECTURE OF A WSN. ... 14
FIGURE 5 PHASES OF LEACH AND ITS VARIANTS IN WSNS. ... 26
FIGURE 6 THREE DIMENTIONS OF ATTACKS INTERVENTION AND POSSIBLE COMBINATIONS. ... 28
FIGURE 7 INTERVENTION LEVELS WHERE X →Y MEANS Y INCLUDES ALL ATTACKER BEHAVIOR OF X. ... 30
FIGURE 8 THE DIVISION OF PROCESSES OF THE DISTRIBUTED WM ALGORITHM ... 38
FIGURE 9 AN EXAMPLE OF A BLOOM FILTER.. ... 39
FIGURE 10 IDS OPRATION USING BLOOM FILTERS. ... 40
FIGURE 11 FSM TO DETECT UNMATCHED RREQ AND RREP MESSAGES. ... 41
FIGURE 12 ILLUSTRATION OF NORMAL AND MPR FORWARDING. ... 42
FIGURE 13 PROPOSED IDS FLOWCHART FOR REGULAR NODES IN THE NETWORK. ... 49
FIGURE 14 PROPOSED IDS FLOWCHART FOR CHS IN THE NETWORK. ... 51
FIGURE 15 THE ROUTING PROTOCOLS SIMULATOR USED TO EVALUATE OUR IDS. ... 52
FIGURE 16 IMPACT OF DENSITY ON MALICIOUS NODES’ TRUE DETECTION RATE. ... 55
FIGURE 17 IMPACT OF DENSITY ON FALSE POSITIVE DETECTION RATE. ... 56
FIGURE 18 IMPACT OF DENSITY ON PRECISION, RECALL AND ACCURACY. ... 57
FIGURE 19 IMPACT OF DENSITY, UNIFORM PACKET LOSS ON TRUE POSITIVE RATE. ... 58
FIGURE 20 IMPACT OF DENSITY, UNIFORM PACKET LOSS ON FALSE POSITIVE RATE. ... 59
FIGURE 21 IMPACT OF DENSITY, UNIFORM PACKET LOSS ON PRECISION, RECALL AND ACCURACY. ... 60
FIGURE 22 IMPACT OF UNIFORM PACKET LOSS ON TRUE POSITIVE DETECTION RATE. ... 61
FIGURE 23 IMPACT OF UNIFORM PACKET LOSS ON FALSE POSITIVE RATE. ... 62
FIGURE 24 IMPACT OF UNIFORM PACKET LOSS ON PRECISION, RECALL AND ACCURACY. ... 63
FIGURE 25 IMPACT OF THE NUMBER OF CHANCES ON THE FALSE POSITIVE RATE. ... 64
FIGURE 26 IMPACT OF DENSITY AND RANDOM PACKET LOSS (LEFT FIGURE), AND UNIFORM PACKET LOSS (RIGHT FIGURE) ON THE FALSE POSITIVE AND THE FALSE NEGATIVE RATES. ... 65
FIGURE 26 IMPACT OF DENSITY AND UNIFORM PACKET LOSS ON THE FALSE POSITIVE AND THE FALSE NEGATIVE RATES. ... 66
T
ABLES LIST
TABLE 1 COMPARISON BETWEEN TRADITIONAL NETWORKS AND WSNS ... 197
General introduction
Nowadays, the investigation of the Wireless Sensor Network (WSN) has materialized its functional area in various fields such as environmental engineering, industrial and business applications, military, feedstock and habitat, agriculture sector, seismic detection, intelligent buildings, smart grids, and predictive maintenance, etc. Although some challenges still exist in the wireless sensor network, in spite of the shortcoming, it has been gaining significant attention among researchers and technologists due to its adaptability and robustness.
In this thesis, our goal was to study the security issues in WSNs and to propose an intrusion detection system that could protect the network from certain attacks. Usually, WSNs’ conditions are harsh and cannot be controlled which makes them targeted by many harmful attacks aiming to collect data, falsify it, disable a functionality of some sensors in the network or the whole network itself. This is the reason why many intrusion prevention and detection systems were developed to identify attackers and eventually stop them.
This thesis is presented in three chapters: the first one, “introduction to wireless sensor networks”, gives an overview of WSNs’ basic concepts, challenges and applications, discusses the routing process and security issues in WSNs. The second chapter, “intrusion detection systems in WSNs”, defines what an intrusion detection system (IDS) is, gives classification and detailed examples for such systems in literature and focuses at the end on the dropping packets’ IDSs as it was the topic of our research. The final chapter, “the proposed IDS and its evaluation”, is dedicated to the description of the proposed IDS, metrics of its evaluation, and simulations’ results and discussion. A general conclusion ends this work and discusses global results and future work we would like to accomplish.
8
I CHAPTER
I
Introduction to
Wireless Sensor
Networks
(WSNs)
9
I.1
IntroductionWireless Sensor Networks (WSNs) are gaining a lot of attention from researchers due to their massive applications. In this chapter, an overview of Wireless Sensor Networks (WSNs) is presented. First, a sensor node is defined as well as its components. Then, a WSN is defined, its architectures and design constraints and challenges, its applications and finally, security issues to which it is exposed.
I.2
Sensing and sensorsSensing is a technique used to gather information about a physical object or process, including the occurrence of events (i.e. changes in state such as a drop in temperature or pressure). An object performing such a sensing task is called a sensor. From a technical perspective, a sensor is a device that translates parameters or events in the physical world into signals that can be measured and analyzed [1].
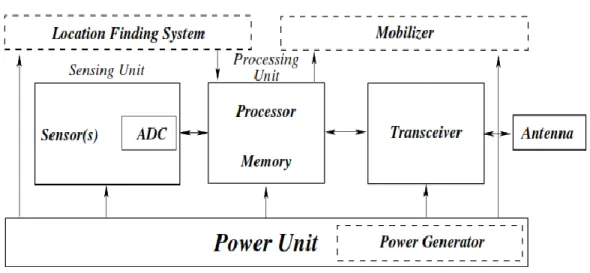
The general architecture and the major components of a wireless sensor device (node) are illustrated in Figure 1. A wireless sensor device is generally composed of four basic components: a sensing unit, a processing unit, a transceiver unit and a power unit. Moreover, additional components can also be integrated into the sensor node depending on the application. These components as shown by the dashed boxes in Figure 1 including a location finding system, a power generator, and a mobilizer. Next, each component is described in detail [2].
Sensing unit
The sensing unit is the main component of a wireless sensor node that distinguishes it from any other embedded system with communication capabilities. The sensing unit may generally include several sensor units, which provide information gathering capabilities from the physical world. Each sensor unit is responsible for gathering information of a certain type, such as temperature, humidity, or light, and is usually composed of two subunits: a sensor and an analog-to-digital converter (ADC). The analog signals produced by the sensor based on the observed phenomenon are converted to digital signals by the ADC, and then fed into the processing unit.
Processing unit
The processing unit is the main controller of the wireless sensor node, through which every other component is managed. The processing unit may consist of an on-board memory or may be associated with a small storage unit integrated into the embedded board. The processing unit
10 manages the procedures that enable the sensor node to perform sensing operations, run associated algorithms, and collaborate with the other nodes through wireless communication.
Transceiver unit
Communication between any two wireless sensor nodes is performed by the transceiver units. A transceiver unit implements the necessary procedures to convert bits to be transmitted into radio frequency (RF) waves and recover them at the other end. Essentially, the sensor node is connected to the network through this unit.
Power unit
One of the most important components of a wireless sensor node is the power unit. Usually, battery power is used, but other energy sources are also possible. Each component in the wireless sensor node is powered through the power unit and the limited capacity of this unit requires energy-efficient operation for the tasks performed by each component.
Location finding system
Most of the sensor network applications, sensing tasks, and routing techniques need knowledge of the physical location of a node. Thus, it is common for a sensor node to be equipped with a location finding system. This system may consist of a GPS (Global positioning system) module for a high-end sensor node or may be a software module that implements the localization algorithms that provide location information through distributed calculations.
Mobilizer
A mobilizer may sometimes be needed to move sensor nodes when it is necessary to carry out the assigned tasks. Mobility support requires extensive energy resources and should be provided efficiently. The mobilizer can also operate in close interaction with the sensing unit and the processor to control the movements of the sensor node.
Power generator
While battery power is mostly used in sensor nodes, an additional power generator can be used for applications where longer network lifetime is essential. For outdoor applications, solar cells are used to generate power. Similarly, energy scavenging techniques for thermal, kinetic, and vibration energy can also be used .
11
Figure 1 Architecture of a sensor node
.
I.3
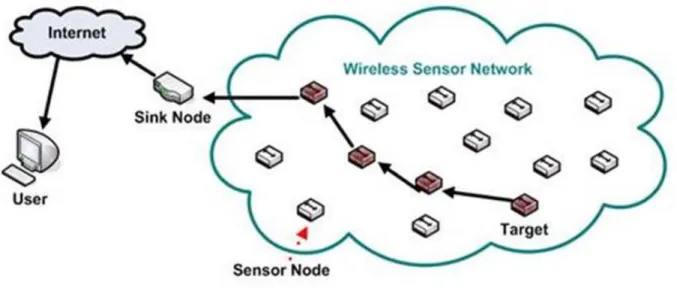
Wireless Sensor Networks (WSNs)Wireless Sensor Networks (WSNs) can be defined as a self-configured and infrastructureless wireless networks to monitor physical or environmental conditions, such as temperature, sound, vibration, pressure, motion or pollutants and to cooperatively pass their data through the network to a main location or sink where the data can be observed and analyzed. A sink or base station acts like an interface between users and the network Figure 2. One can retrieve required information from the network by injecting queries and gathering results from the sink. Typically, a wireless sensor network contains hundreds of thousands of sensor node [3].
I.4
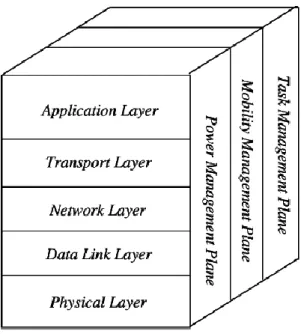
WSNs StructureStructure of Wireless Sensor Networks Wireless sensor networks follows the most common architecture: OSI model. Basically, there are five layers in sensor network (Figure 3). These are application layer, transport layer, network layer, data link layer and physical layer. There are three cross layers planes added to those above five layers of OSI model: power management plane, connection management plane, and task management plane. These layers are used to manage the network connectivity and allows the nodes to work together to increase the overall efficiency of the network. [4] explained briefly each layer as follows:
12
Figure 2 Elements of a WSN
.
Transport LayerThe function of this layer is to provide congestion avoidance and reliability and there are a lot of protocols designed to provide this function.. The basic function of this layer is to accept data from above layers and split it up into smaller units then pass these to the network layer and ensure the delivery of all pieces at the other end. It contains a variety of protocols like TCP, UDP, SCTP, DCCP, SPX.
Network Layer
The major function of the network layer is routing. This layer has a lot of challenges depending upon the application but probably, the major challenges are in the limited memory and buffers, power saving, sensor does not have a global ID and have to be self-organized. This is unlike computer networks with IP address and central device for controlling. The basic idea of the routing protocol is to define a reliable path and redundant paths according to a certain scale called metric, which is distinct from a protocol to another. There are various routing protocols available for this layer, they can be divide into; flat routing such as direct diffusion and hierarchal routing e.g. LEACH or can be divided into time driven, event driven and query driven. In continuous time driven protocol, the data is sent periodically. This kind of protocol is for applications that need a periodic monitoring. In event driven and query driven protocols, the sensor broadcast data according to a specific action or user query.
13
Figure 3 Common structure of a WSN
.
Data link layerThe data link layer is there to maintain the error correction and error detection mechanisms. It is also accountable for the multiplexing of data, having access to it and the error control.
Physical layer
Physical layer can provide an interface to transmit a stream of bits over physical medium. Responsible for generating carrier frequencies, frequency selection, signal detection, signals modulation and data encryption.
Application layer
Responsible for traffic management and provide software for different applications that translate the data in an understandable form or send queries to obtain information. It contains a variety of protocols like NNTP, SIP, SSI, DNS, FTP, GOPHER, NFS, NTP, SMTP, SMPP, ANMP and TELNET.
The three cross planes or layers are:
Power management plane
It is responsible for managing the power level of sensor nodes for processing, sensing and communication.
Connection management plane
It is responsible for configuration or reconfiguration of sensor nodes in attempt to establish or maintain network connectivity.
14
Task management plane
It is responsible for distribution of tasks among sensor nodes to prolong network lifetime and improve energy efficiency.
I.5
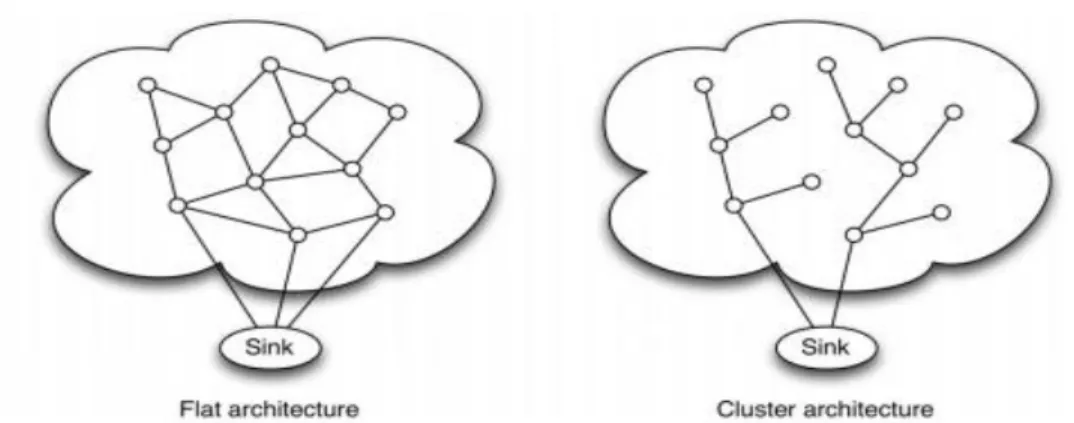
WSNs ArchitectureA WSN is usually composed of a large number of nodes deployed in a region of interest. In a typical scenario, the region of interest is often a harsh environment, and the nodes are randomly deployed. The sensed data is transmitted through the nodes up to special entities called sinks. The sinks are nodes with two or more network interfaces that act as gateway between the WSN and the user network (e.g. internet). The sink usually collects and processes the data from the network sending only relevant information to the user. It also receives commands from the user to be executed on the internal network. A sensor node can communicate directly to the sink (single-hop) or use a multi-hop communication passing the information to its neighbor. Single-hop communication leads to long distance transmission, resulting a high energy consumption. Using multi-hop communication is possible to reduce the transmission distance and increase the network lifetime. In multi-hop transmission, the network architecture plays a major role. Multi-hop network architectures are typically divided into flat or hierarchical as represented in Figure 4 [5].
Figure 4 Architecture of a WSN
.
In flat architecture, each node plays the same role in sensing and transmitting the information. In hierarchical architectures, the nodes are organized into clusters. In each cluster, one or more nodes (head node) are responsible to communicate with other clusters or directly to the sink. The head node may be dynamically selected by various criteria, including its available energy, distance between cluster members and other cluster heads, and node homogeneity.
15
I.6
Challenges and ConstraintsWhile sensor networks share many similarities with other distributed systems, they are subject to a variety of unique challenges and constraints. These constraints impact the design of a WSN, leading to protocols and algorithms that differ from their counterparts in other distributed systems. [1] described the most important design constraints of a WSN.
I.6.1 Energy
The constraint that is most often associated with sensor network design is the fact that sensor nodes operate with limited energy budgets. Typically, they are powered through batteries, which must be either replaced or recharged (e.g., using solar power) when depleted. For some nodes, neither option is appropriate, that is, they will simply be discarded once their energy source is depleted. Whether the battery can be recharged or not significantly affects the strategy applied to energy consumption. For non-rechargeable batteries, a sensor node should be able to operate until either its mission time has passed or the battery can be replaced. The length of the mission time depends on the type of application, for example, scientists monitoring glacial movements may need sensors that can operate for several years while a sensor in a battlefield scenario may only be needed for a few hours or days.
I.6.2 Self-Management
It is the nature of many sensor network applications that they must operate in remote areas and harsh environments, without infrastructure support or the possibility for maintenance and repair. Therefore, sensor nodes must be self-managing. In that, they configure themselves, operate and collaborate with other nodes, and adapt to failures, changes in the environment, and changes in the environmental stimuli without human intervention.
I.6.3 Wireless Networking
The reliance on wireless networks and communications poses a number of challenges to a sensor network designer. For example, attenuation limits the range of radio signals, that is, a radio frequency (RF) signal fades (i.e., decreases in power) while it propagates through a medium and while it passes through obstacles. As a consequence, an increasing distance between a sensor node and a base station rapidly increases the required transmission power. Therefore, it is more energy-efficient to split a large distance into several shorter distances, leading to the challenge of supporting multi-hop communications and routing. Multi-hop communication requires that nodes in a network cooperate with each other to identify efficient routes and to serve as relays. This challenge is further exacerbated in networks that employ duty cycles to preserve energy. That is,
16
many sensor nodes use a power conservation policy where radios are switched off when they are not in use.
I.6.4 Decentralized Management
The large scale and the energy constraints of many wireless sensor networks make it infeasible to rely on centralized algorithms (e.g., executed at the base station) to implement network management solutions such as topology management or routing. Instead, sensor nodes must collaborate with their neighbors to make localized decisions, that is, without global knowledge. As a consequence, the results of these decentralized (or distributed) algorithms will not be optimal, but they may be more energy-efficient than centralized solutions. Consider routing as an example for centralized and decentralized solutions. While a decentralized approach may lead to nonoptimal routes, overheads in a centralized routing can be reduced significantly.
I.6.5 Design Constraints
While the capabilities of traditional computing systems continue to increase rapidly, the primary goal of wireless sensor design is to create smaller, cheaper, and more efficient devices. Driven by the need to execute dedicated applications with little energy consumption, typical sensor nodes have the processing speeds and storage capacities of computer systems from several decades ago. The need for small form factor and low energy consumption also prohibits the integration of many desirable components, such as GPS receivers. These constraints and requirements also impact the software design at various levels, for example, operating systems must have small memory footprints and must be efficient in their resource management tasks. A sensor’s hardware constraints also affect the design of many protocols and algorithms executed in a WSN. For example, routing tables that contain entries for each potential destination in a network may be too large to fit into a sensor’s memory. Instead, only a small amount of data (such as a list of neighbors) can be stored in a sensor node’s memory. Further, while in-network processing can be employed to eliminate redundant information, some sensor fusion and aggregation algorithms may require more computational power and storage capacities than can be provided by low-cost sensor nodes. Therefore, many software architectures and solutions (operating system, middleware, network protocols) must be designed to operate efficiently on very resource-constrained hardware.
I.6.6 Security
Many wireless sensor networks collect sensitive information. The remote and unattended operation of sensor nodes increases their exposure to malicious intrusions and attacks. Further, wireless communications make it easy for an adversary to eavesdrop on sensor transmissions.
17
For example, one of the most challenging security threats is a denial-of-service attack, whose goal is to disrupt the correct operation of a sensor network. This can be achieved using a variety of attacks, including a jamming attack, where high-powered wireless signals are used to prevent successful sensor communications. The consequences can be severe and depend on the type of sensor network application. While there are numerous techniques and solutions for distributed systems that prevent attacks or contain the extent and damage of such attacks, many of these incur significant computational, communication, and storage requirements, which often cannot be satisfied by resource-constrained sensor nodes. As a consequence, sensor networks require new solutions for key establishment and distribution, node authentication, and secrecy.
I.6.7 Other Challenges
From the discussion so far, it becomes clear that many design choices in a WSN differ from the design choices of other systems and networks. Table 1 summarizes some of the key differences between traditional networks and wireless sensor networks. A variety of additional challenges can affect the design of sensor nodes and wireless sensor networks. For example, some sensors may be mounted onto moving objects, such as vehicles or robots, leading to continuously changing network topologies that require frequent adaptations at multiple layers of a system, including routing (e.g., changing neighbor lists), medium access control (e.g., changing density), and data aggregation (e.g., changing overlapping sensing regions). A heterogeneous sensor network consists of devices with varying hardware capabilities, for example, sensor nodes may have more hardware resources if their sensing tasks require more computation and storage or if they are responsible for collecting and processing data from other sensors within the network. Also, some sensor applications may have specific performance and quality requirements, for example, low latencies for critical sensor events or high throughput for data collected by video sensors. Both heterogeneity and performance requirements affect the design of wireless sensors and their protocols. Finally, while traditional computer networks are based on established standards, many protocols and mechanisms in wireless sensor networks are proprietary solutions, while standards-based solutions emerge only slowly. Standards are important for interoperability and facilitate the design and deployment of WSN applications; therefore, a key challenge in WSN design remains the standardization of promising solutions and the harmonization of competing standards.
18
I.7
WSNs ApplicationsWireless sensor networks provide practical usefulness in developing a large number of applications, including the protection of civil infrastructures, habitat monitoring, precision agriculture, health care, and many more. [6] summarized all these in a short list:
I.7.1 Military applications
Monitoring inimical forces
Monitoring friendly forces and equipment Military-theater or battlefield surveillance Targeting
Battle damage assessment
Nuclear, biological, and chemical attack detection and more ...
I.7.2 Environmental applications
Microclimates Forest fire detection Flood detection
Precision agriculture and more ...
I.7.3 Health applications
Remote monitoring of physiological data
Tracking and monitoring doctors and patients inside a hospital Drug administration
Elderly assistance and more ...
I.7.4 Home applications
Home automation
Instrumented environment
Automated meter reading and more ...
I.7.5 Commercial applications
Environmental control in industrial and office buildings Inventory control
Vehicle tracking and detection Traffic flow surveillance and more ...
19
Traditional networks Wireless sensor networks
General-purpose design serving many applications
Single-purpose design serving one specific application
Typical primary design concerns are network performance and latencies energy is not a primary concern
Energy is the main constraint in the design of all nodes and network components
Networks are designed and engineered according to plans
Deployment, network structure and resource use are often ad hoc (without planning)
Devices and networks operate in controlled and mild environments
Sensor networks often operate in environment with harsh conditions
Maintenance and repair are common and networks are typically easy to access
Physical access to sensor nodes is often difficult or even impossible
Component failure is addressed through maintenance and repair
Component failure is expected and addressed in the design of the network
Obtaining global network knowledge is typically feasible and centralized management is possible
Most decisions are made localized without the support of a central manager
Table 1 Comparison between traditional networks and WSNs
I.8
Routing in WSNRouting process is the major task after sensing data in a WSN as it represents the key role of a WSN which is transmitting sensed events (data) to the base station where it can be processed. In this section, we will describe types of routing protocols and how they were categorized.
I.8.1 Types of routing protocols
Routing protocols play an important role in the energy efficiency of WSNs as they contribute to the reduction of energy consumption and latency and they provide high data throughput and quality of service for the sensor network.
[7] classified routing protocols according to the network structure to flat routing, hierarchical routing, and location-based routing. According to the protocol operation, they enumerated multipath-based, query-based, negotiation-based, QoS-based, and coherent-based routings. Here is the definition they gave for each category of protocols:
Network Structure
The network structure describes the characteristics of a network, which can be divided into two groups; the characteristics of base stations and the characteristics of sensor nodes.
20
Flat based
In these networks, all nodes play the same role and there is absolutely no hierarchy.
Hierarchical based
This class of routing protocols sets out to attempt to conserve energy by arranging the nodes into clusters.
Location based
Most of the routing protocols for sensor networks require location information of nodes which is needed to calculate the distance between two particular nodes so that energy consumption can be estimated.
Protocol Operation
It describes the main operational characteristics of a routing protocol; in terms of communication pattern, hierarchy, delivery method, computation, next- hop.
Multipath based
In this case, the network derives benefit from the fact that there may be multiple paths between a node and the destination.
Query based
Here the focus lies on propagation of queries throughout the network by the nodes which require some data.
Negotiation based
In negotiation based protocols, the nodes exchange a number of messages between themselves before transmission of data.
QoS-based
QoS based protocols have to find a trade-off between energy consumption and the quality of service.
Coherent-based
Coherence based protocols focus on how much data processing takes place at each node.
I.8.2 LEACH protocol and variants
As the battery life is one of the main challenges in WSNs, routing protocols have to be efficient concerning energy consumption. Cluster based routing protocols like Low Energy Adaptive Clustering Hierarchy (LEACH), Hybrid Energy Efficiency Protocol (HEEP), and
21 Threshold sensitive Energy Efficient Network protocol (TEEN) efficiently manage the energy usage.
We chose LEACH as a basis for our implementations in this work as it is still gaining attention by researchers. In fact, more and more variants of LEACH are suggested in order to overcome certain drawbacks like security breaches or to suit different applications like multi hop routing in dense networks. This section describes in detail LEACH protocol and some of its variants.
LEACH [8]
LEACH is a pioneer clustering routing protocol for WSN. It is a self-organizing, adaptive clustering routing protocol that uses randomization to distribute the energy load evenly among the sensors in the network. In LEACH, the nodes organize themselves into local clusters, with one node acting as the local base station or cluster-head (CH).
The operation of LEACH consists of several rounds where each round is divided into two phases: the set-up phase and the steady state phase. We describe what each of these phases includes as steps.
set-up phase
During the set-up phase, CH selection, cluster formation and assignment of a TDMA (Time Division Multiple Access) schedule by the CH for member nodes are performed.
In CH selection, each node participates in a CH election process by generating a random priority value between 0 and 1. If the generated random number of a sensor node is less than a threshold value T(n) then that node becomes CH. The value of T(n) is calculated using equation 1:
𝑇(𝑛) = {
𝑃 1−𝑃∗(𝑟 𝑚𝑜𝑑𝑃1)∶ 𝑖𝑓 𝑛 ∈ 𝐺
0 ∶ 𝑜𝑡ℎ𝑒𝑟𝑤𝑖𝑠𝑒
………(1)
Where P denotes the desired percentage of sensor nodes, to become CHs among all sensor nodes, r denotes the current round and G is the set of sensor nodes that have not participated in CH election in previous 1/P rounds. A node that becomes the CH in round r cannot participate in the next 1/P rounds. This way, every node gets equal chance to become the CH and energy dissipation among the sensor nodes is distributed uniformly. Once a node is selected as the CH, it broadcasts an advertisement message to all other nodes.
22 Depending on the received signal strength of the advertisement message, sensor nodes decide to join a CH for the current round and send a join message to this CH. By generating a new advertisement message based on equation 1, CHs rotate in each round in order to evenly distribute the energy load in the sensor nodes. After the formation of the cluster, each CH creates a TDMA schedule and transmits these schedules to their members within the cluster. The TDMA schedule avoids the collision of data sent by member nodes and permits the member nodes to go into sleep mode. The set-up phase is completed if every sensor node knows its TDMA schedule. The steady state phase follows the set-up phase.
steady state phase
In the steady state phase, transmission of sensed data from member nodes to the CH and then from the CH to the BS are performed using the TDMA schedule. Member nodes send data to the CH only during their allocated time slot. While a member node sends data to the CH during its allocated time slot, all other member node of that cluster remains in the sleep state. This property of LEACH reduces intra cluster collision and energy dissipation which increases the battery life of all member nodes. Additionally, CHs aggregate data received from their cluster members and send it directly to the BS. Transmission of data from the CH to the BS is also performed with the help of the allocated TDMA schedule. The CH senses the states of the channel for sending its data. If the channel is busy i.e. it is being used by any other CH then it waits; otherwise it uses the channel to transmit the data to the BS.
Sec-LEACH [9]
This protocol shows how random key pre distribution, usually studied in the context of flat networks, can be used to secure communication in hierarchical (cluster-based) protocols such as LEACH.
In their solution, [9] proposed to generate a large pool of S keys and their ids prior to network deployment. For each node X, a pseudo random function generates its unique id idX. Then a
sequence of m numbers is randomly generated for each idX. The set of key ids assigned to X, can
then be obtained by mapping each number in the sequence to its correspondent value modulus S. Also prior to deployment, for each node is assigned a pairwise key shared with the BS.
The LEACH clustering algorithm can then be run with the following modifications: when a self-elected CH broadcasts its ADV message, it includes the ids of the keys in its key ring; the remaining nodes now cluster around the closest CH with whom they share a key. The shared keys
23 with the BS are used to route aggregated data from CHs to the BS. Sec-LEACH includes a counter in routed packets to guarantee freshness and prevent replaying attacks.
A-LEACH (Armor-LEACH) [10]
A-LEACH is a combination between Sec-LEACH protocol and TCCA algorithm (Time Controlled Clustering Algorithm). Prior to network deployment, A-LEACH assigns to each node
m keys to communicate with other regular nodes and a pairwise key to assure routing to the BS,
exactly like Sec-LEACH. But unlike Sec-LEACH protocol, A-LEACH uses a new equation to calculate the probability of a node to become a CH, the TCCA CH election equation:
𝑇(𝑛) = { 𝑚𝑎𝑥 ( 𝑃 1−𝑃∗(𝑟 𝑚𝑜𝑑1𝑃) ∗ 𝑅𝑒𝑚𝐸𝑛𝑔 𝑀𝑎𝑥𝐸𝑛𝑔, 𝑇𝑚𝑖𝑛) ∶ 𝑖𝑓𝑆𝜖𝐺 0 ∶ 𝑜𝑡ℎ𝑒𝑟𝑤𝑖𝑠𝑒 ………..(2)
Where P is the desired percentage of CHs, Tmin is a minimum threshold (to avoid the
possibility of remaining energy shortage), and G is the set of sensors that have not became CHs in 1/P round.
Introducing the remaining energy as a parameter in the new equation gives a better chance to nodes with more energy to become CHs and this helps balancing energy between nodes in the network.
LEACH-B (LEACH-Balanced) [11]
LEACH-B protocol resolves the issue of unbalanced clusters of basic LEACH. It uses the concept of the second selection of CH for modifying the CH at set-up phase in each round. After deciding the desired percentage of sensor nodes to become the CH, LEACH-B proposes another competition for CH selection. According to LEACH-B, CHs in each round should be a constant number N ∗ P, where P is the desired percentage of CHs and N is the number of sensor nodes. In this protocol, first CHs are selected randomly based on LEACH protocol, and then each CH broadcasts its status and residual energy to each sensor node. Now there are two possibilities. First, if the number of randomly selected CHs is less than N ∗ P, then some normal nodes with less time interval are selected as CHs into a CH set and these selected CHs broadcast their CH status to the network. The time interval is calculated by t = K/E where E represents residual energy of an individual sensor node and K is a constant factor. Second, if randomly selected CHs are more than N ∗ P, then exclude some CHs with low energy to maintain the CH set equal to N ∗ P. To achieve this, all the CHs are arranged in descending order based on their residual energy. The CHs that are ranked lower than N ∗ P convert into normal nodes.
24
MH-LEACH (Multi-hop-LEACH) [12]
One of the main goals of the algorithm is to find possible routes for a cluster-head (leader) to send a packet using other cluster-heads in order to save its energy [12]. This proposal takes into account the fact that the higher the signal strength of the received packet, i.e., Received Signal Strength Indicator (RSSI), the greater the proximity of the node that sent the message. This information is used in order to build the routing table for each cluster-head. The MH-LEACH proposes the routes establishment using two phases:
Phase 1: The cluster-heads are defined as a part of LEACH algorithm. After that, they broadcast an announcement message and all the cluster-headers in the transmission ratio will take the advantage in order to construct their routing table taking in account the level of signal (RSSI) received. So, they organize their early routes containing the closest cluster-heads to send a packet.
Phase 2: After that, each leader sends these initial routes (from routing table) to the base station that will check whether a cluster-head can be in the route of another one. After this check, the base station sends their routes back to the nodes.
Since the first phase is distributed, constructed routing tables do not contain necessarily the correct routes. In fact, each CH defines the closest CHs as their next relays to send packets to BS without knowing if they are transmitted in the right direction of the BS or the opposite one. Another example of wrong routes is loops in the network. If a CH 1 has as a first route CH 2, and CH 2 has as a first route CH 1, both nodes energy is wasted transferring the same packet in a loop. That’s why the second phase is essential to correct the routing tables.
LEACH-L (Advance Multi-hop Low Energy Adaptive Clustering Hierarchy) [13]
Unlike MH-LEACH, LEACH-L adopts a solution for constructing the correct routing tables instead of sending the wrong ones to the BS to be corrected. [13] explains that each node can directly choose as a next relay (next CH to transmit data to the BS) the closest one to the BS with the best energy status.
This kind of protocols assumes that each node in the network knows exactly their spatial coordinates. For this, one of the processes of determining the location is used (GPS (Global positioning system), triangulation…etc.).
LEACH-1R (LEACH One Round) [14]
Instead of wasting energy electing CHs and sending joining requests every round in LEACH, [14] proposed to keep elected CHs until their remaining energy is run out or under a certain
25 threshold. Moreover, the new CH is selected directly among the cluster members taking into consideration the strength of the last received signal.
Results in [14] confirmed that avoiding the repeated regular process of CH election and joining clusters reduces the energy consumption and so increases the network lifetime.
I.8.3 Discussion
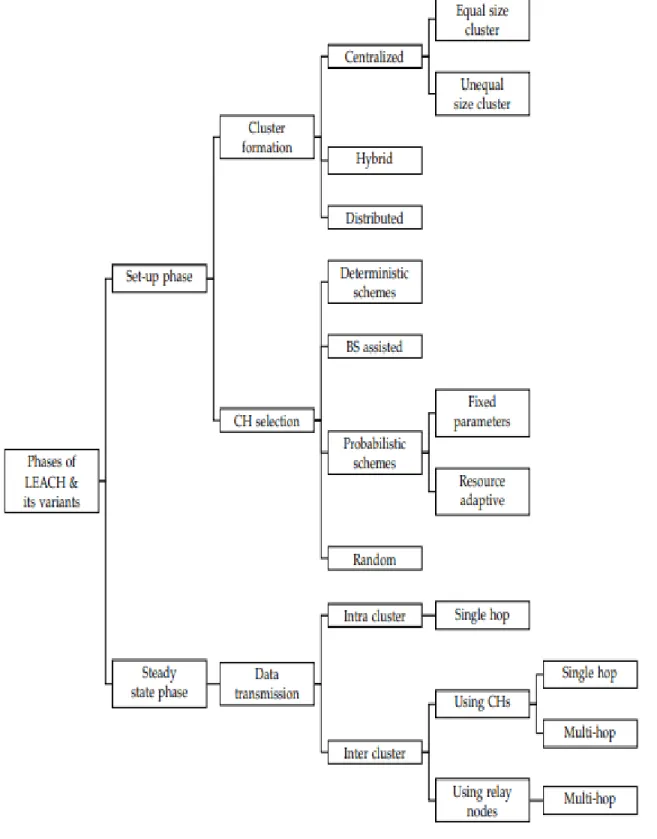
Figure 5 summarizes the functioning of LEACH steps and its variants [15]. The following briefly discusses advantages and drawbacks of each protocol we have seen.
LEACH is a complete distributed routing protocol which is great in terms of energy consumption so it does not require any global information. Advantages of LEACH are the clustering concept and data aggregation technique which assure both less communication and increase the network lifetime. The allocation of TDMA schedule by CHs to member nodes allows the member nodes to go into sleep mode which prevents intra cluster collisions and enhances the battery lifetime of sensor nodes. Another great point of LEACH protocol is the equal chance given to every sensor node to become the CH which balances remaining energy and enhances also the network lifetime.
However, LEACH protocol has quite many disadvantages. One of these is the equal chance nodes have to become CHs without taking into consideration their energy level. Another drawback of LEACH is the randomized CH election that gives no guarantee on neither the number of CHs elected nor their position and distribution in the network.
LEACH variants can use single hop or multi hop routing. Single hop routing protocols we have seen in the previous section (LEACH, Sec-LEACH, LEACH-B) are not practical in large scale networks because BS is not within the transmission range of all CHs. This makes them suited only for small WSNs. Still, they demand less communication than multi hop protocols and so, they save more energy.
26
Figure 5 phases of LEACH and its variants in WSNs
.
I.9
Security in WSNsSecurity in WSNs is an element not to neglect as deployment conditions for these networks cannot be controlled which makes them vulnerable to many kinds of intentional harmful attacks. This section discusses the model of attacks a WSN can face, the impact of these attacks on
27 elements of the network (nodes), and finally, some common attacks, their goals and how they operate.
I.9.1 Attacks model
In sensor networks security, an attacker can perform a wide variety of attacks. Not all of them have the same goal or motivations. So, in order to plan and design better defense systems, [16] formulates a threat model that distinguishes between two types of attacks: outsider attacks and insider attacks. We now treat each one of these classes in turn.
Outsider Attacks
In an outsider attack (intruder node attack), the attacker node is not an authorized participant of the sensor network. Authentication and encryption techniques prevent such an attacker to gain any special access to the sensor network. The intruder node can only be used to launch passive attacks (passive eavesdropping, i.e. listening and recording packets for analyzing, denial of service attacks where the network is jammed with high-energy broadcasting that disrupt the communication operations , replay attacks where the attacker captures exchanged packets and resends them in the network).
Insider Attacks
Perhaps more dangerous from a security point of view is an insider attack, where an adversary by physically capturing a node and reading its memory, can obtain its key material and forge node messages. Having access to legitimate keys, the attacker can launch several kinds of attacks without easily being detected (false data injection, Selective reporting by dropping willingly some of the packets).
I.9.2 Attacks Impact on nodes
Each attack can influence the network system properties in time according to their goal or manipulation. We can count three major classes of system properties whose influence can corrupt the normal activity of the WSN: safety, liveness, and information flow. [17] explained that safety properties describe what is not allowed to happen, liveness properties demand what eventually must happen, and information flow properties specify the type and amount of information flow in security environments. Here are details on how an attacker can change each major property [17]:
Safety
Safety properties affection can go from disturbing certain parts of the node state to changing its whole code. An example of this is changing data, read or contained, in a node.
28
Liveness
An attacker can prevent the node from executing further processing temporarily (crash-recovery) or permanently (crash). These changes can remove nodes totally from the network or disable them when they are the most needed (routing data for example).
Information flow
The network can be observed by the attacker, i.e. content of messages from or to a node is revealed to the intruder. The memory data can also be looked into. This information leaking makes the system vulnerable to easy intrusion (replaying messages, injecting false information..etc.).
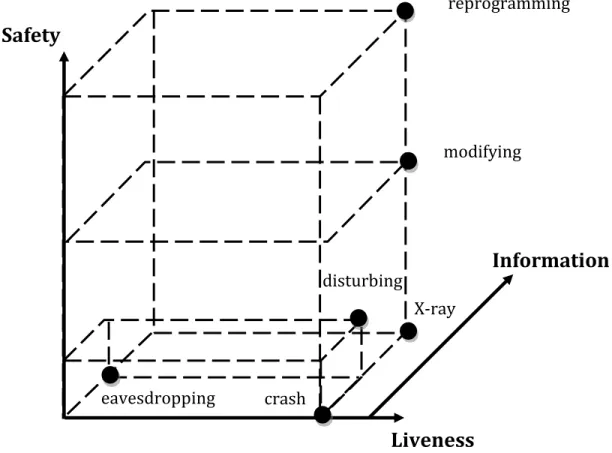
[18] defined a three dimensional property space based on those three classes of properties on which they placed each type of attack (black dots) according to their aim and impact on the network (Figure 6). The following is a review of each type of attack definition and its impact on the WSN.
Figure 6 three dimentions of attacks intervention and possible combinations. Crashing
If the crashing attack has not the ability to change safety and information flow properties, it changes completely the liveness properties of the node: the node may stop or resume step
Liveness
Information
Safety
reprogramming modifying X-ray disturbing crash eavesdropping29 execution at any time. This is actually possible through the physical access to nodes in the network.
Eavesdropping
This kind of attack only changes the information flow properties through access to the messages content in transit.
X-raying
The X-raying attack combines crashing with complete change of information flow properties. The attacker has full access to memory (data and code) of the node, can eavesdrop on all communication, but cannot change the node safety in any way.
Disturbing
It’s a combination between crashing, eavesdropping, and limited state perturbation. This kind of attack can change routing tables, delete, inject replay and spoof packets, but it cannot have an access to program memory.
Modifying
The modifying attacker combines the X-raying and full state perturbation. The attacker has full access to data in memory but not the code.
Reprogramming
This kind of attack gathers all previous attacks together: it’s the maximum level of attacker intervention in the network.
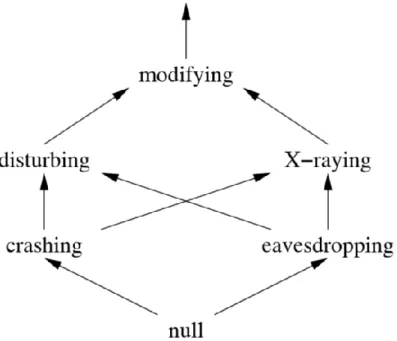
Figure 7 shows how each attack can be included in another one according to their impact on the WSN [19].
30
Figure 7 intervention levels where X →Y means Y includes all attacker behavior of X.
I.9.3 Common attacks in WSN
Well known possible attacks to harm the network and make it unreliable for communication and proper functioning were briefly described in [19]:
Jamming
Jamming attack is related with disrupting or interfering the radio frequencies used by sensor nodes. Attacker may get physical access to some nodes and creates jam in the network to disrupt the network. Jamming attack comes under physical layer attack.
Tampering
Refers to gaining physical access to a set of sensors by tampering with their hardware configuration and making nodes to act as adversary node. Tampering is possible at physical layer.
Sybil Attack
Sybil attack is defined as a malicious device illegitimately taking on multiple identities. In Sybil attack, an adversary can appear to be in multiple places at the same time. A single node presents multiple identities to other nodes in the sensor network either by fabricating or stealing the identities of authenticated nodes. It is a Network layer attack.
31
Wormhole Attack
Wormhole attack is a critical attack in which the attacker records the packets (or bits) at one location in the network and tunnels those to another location. This generates a false scenario that the original sender is in the neighborhood of the remote location. The tunneling procedure forms wormholes in a sensor network. The tunneling or retransmitting of bits could be done selectively.
Hello Flood Attack
Hello flood attack uses HELLO packets as a weapon to convince the sensors in a WSN of a virtual neighbor. In this type of attack, an attacker with a high radio transmission range (termed as a laptop-class attacker) and processing power sends HELLO packets to a number of sensor nodes which are dispersed in a large area within a WSN.
Black hole Attack
In Black hole attacks, a malicious node acts as a black hole to attract all the traffic in the sensor network through a compromised node or malicious node. A compromised node is placed at the center or any respective position, which looks attractive to neighboring nodes and attracts nearly all the traffic of surrounding nodes that was destined for a base station.
I.10
ConclusionDue to their increasing proved usefulness in various applications, WSNs are targets to many attacks that exploit their limited resources and extreme deployment conditions. Therefore, different techniques must be used to protect data accuracy, network functionality and its availability.
In chapter II, we will discuss Intrusion Detection Systems in WSNs, one of many security measures against attacks aiming to harm WSNs well-functioning.
32
II CHAPTER
II
INTRUSION
DETECTION
SYSTEMS IN
WSNs
33
II.1
IntroductionSince WSNs are vulnerable to many attacks, securing countermeasures are taken to protect both data and the network activity. One of these countermeasures is the Intrusion Detection System (IDS). In this chapter, we will describe what IDSs are and discuss their classifications in literature. We will also see examples of these systems, discuss their functionality and efficiency, and then conclude with a conclusion.
II.2
IDS DefinitionIntrusion detection is the process of monitoring computer networks and systems for violations of security policy (the set of laws, rules, and practices that define the system boundaries and detail exactly what operations are allowed) [20].
An Intrusion detection system (IDS) is defined as a system that tries to detect and alert on attempted intrusions into a system or network [21]. An IDS is composed of IDS agents that run on some or all nodes. The IDS solutions developed for ad-hoc networks cannot be applied directly to sensor networks because the WSN has several specificities. In particular, the computing and energy resources are more constrained on WSN, thus, it is not possible to have an active full-powered agent inside of every node. Also, the IDS must be simple and highly specialized to the specific WSN’s protocols and threats [22].
II.3
IDS ClassificationThere are three basic approaches in intrusion detection systems according to the used detection techniques [23].
Misuse detection technique – Compares the observed behavior with known attack patterns (signatures). Action patterns that may pose a security threat have to be defined and stored in the system. The advantage of this technique is that it can accurately and efficiently detect instances of known attacks, but it lacks an ability to detect an unknown type of attack. Anomaly detection – The detection is based on monitoring changes in behavior, rather
than searching for some known attack signatures. Before the anomaly detection based system is deployed, it usually must be taught to recognize normal system activity (usually by automated training). The system then watches for activities that differ from the learned behavior by a statistically significant amount. The main disadvantage of this type of system is high false positive rate. The system also assumes that there are no intruders during the learning phase.
34 Specification based – The third technique is similar to anomaly detection – it is also based on deviations from normal behavior, but the normal behavior is specified manually as a set of system constraints. Thus there is no learning phase which is particularly difficult in WSNs.
Furthermore, WSNs can be divided into three categories according to IDS topology.
Stand-alone – Each node operates as an independent IDS agent that is responsible for detecting attacks. Individual agents do not cooperate with others and do not share any information. The advantage of this approach is its simplicity and the fact that an attacker is not able to forge any misinformation because nodes don’t rely on others.
Cooperative – Each node still runs its own IDS, but the individual IDSs cooperate between themselves.
Hierarchical – The network is divided into clusters with cluster head nodes. The cluster head has the responsibility for communication with other cluster heads or base stations. The cluster heads can be more powerful or less energy constrained devices than the other nodes. The IDS then only runs on the cluster head node.
II.3.1 Anomaly based IDSs
Anomaly intrusion detection is to detect new or unknown attacks against a computer system, which can be done in a number of ways, such as monitoring network activities, monitoring user or system level behavior. For example, by establishing "profiles" of typical user activities, an IDS can monitor current user activities and compare with established profiles. Whenever a large deviation beyond a predefined threshold is detected, it is reported as the possible intrusion [20].
There are different techniques for anomaly intrusion detection cited in [20]. in the following, we describe IDSs that use statistical and machine learning techniques.
II.3.1.1 Statistical detection based IDSs
Yi-an Huang and Wenke Lee proposed in [24] an IDS that detects four types of intrusion: Intrusion I: Blackhole and Sleep Deprivation using False Source Route and Maximum
Sequence and Rushing. The attacker broadcasts a falsified source route of length 1 from the victim to any node. The advertisement is tagged with Maximum Sequence to defeat valid route messages from the victim. The consequences are that the victim node becomes a blackhole and is in sleep deprivation because it receives and forwards all traffic.
Intrusion II: Selfishness and Denial-of-Service using Packet Dropping. The malicious node
35 intrusion III: Sleep Deprivation using Malicious Flooding. The victim is in sleep deprivation
because it is flooded by a large amount of packets.
Intrusion IV: Routing Loop using Spoofing. The attacker spoofs some route advertisement messages to create a routing loop.
Y. Huang and W. Lee developed in [24] a feature-based analysis for anomaly detection that explores the correlations between each feature and all other features. This approach computes a classifier Ci for each fi using {f1,f2,...,fi−1, fi+1,...,fL}, where {f1,f2,...fL} is the feature set. Ci can be
learned from a set of training data. It predicts the most likely value of fi based on the values of
other features. The original anomaly detection problem, i.e. whether a record is normal or not, is solved as follows. Given a record x =< v1,v2,...,vL >, first apply each Ci to compute
pi(vi|v1,v2,...,vi−1,vi+1,...,vL), i.e. the probability of vi given the values of other features. Then
compute the average probability P of all calculated probabilities pi and compare it with a threshold. An alarm is raised if it is lower than the threshold because it implies the record is highly unlikely.
The authors used 141 features like Flow direction whether it is received, sent, forwarded or dropped, packet type (ROUTE REQUEST, ROUTE REPLY, HELLO…), routes newly added via route discovery, routes in cache with no need to re-discovery and many more listed in [24].
After detecting an anomaly, the IDS must identify the attack type and the attacker whenever possible. Without them, it is hard to determine how to respond meaningfully without interrupting normal communication.
They also proposed identification rules in order to determine each type of attack after anomaly detection.
These identification rules use statistical values of the already seen features within a specific interval of time and number of rounds.
One of the identification rules is for unconditional packet dropping or black hole attacks. It is calculated as follows:
𝐹𝑃
𝑚=
𝑃𝑎𝑐𝑘𝑒𝑡𝑠 𝑎𝑐𝑡𝑢𝑎𝑙𝑙𝑦 𝑓𝑜𝑟𝑤𝑎𝑟𝑑𝑒𝑑𝑃𝑎𝑐𝑘𝑒𝑡𝑠 𝑡𝑜 𝑏𝑒 𝑓𝑜𝑟𝑤𝑎𝑟𝑑𝑒𝑑 ………..(3)
over a sufficiently long time period L. FP determines the ratio of forwarded packets over the packets that are transmitted from M to m and that m should forward. If the denominator is not zero and FPi = 0, the attack is detected as unconditional packet dropping and m is identified as the
attacker.
The same identification rule is used to determine random packet dropping if the value of FPi is
36 Results in [24] showed that the detection rate can go from 78% to 98% and the false alarm rate is about 1%.
II.3.1.2 Machine Learning detection based IDSs
Z. Xiao ET. Al. [25] proposed an IDS that uses throughput, packet loss rate, and the packet average delay of a WSN as the learning featured parameters of intrusion detection. These parameters of a sensor node in normal and anomaly conditions are selected as the learning samples. Then a Bayesian classification as anomaly detection algorithm is used. The following describes the process.
1. Let n-dimensional eigenvector X={x1,x2,…,xn} denote every data sample, to describe n
attributes A1,A2,…,An of the sample.
2. Assumed that the data samples can be divided into m categories C1,C2,…,Cm , we classify
the given data sample X into Ci if and only if
𝑃(𝐶𝒊|𝑋) > 𝑃(𝐶𝒋|𝑋) 1 ≤ 𝑗 ≤ 𝑚, 𝑗 ≠ 𝑖. ...(4)
where the largest category Ci of P(Ci|X) is called the maximum posterior hypothesis. We can
see that from the Bayesian formula, we have P(Ci|X)= P(X|Ci)P(Ci)/P(X)
3. It is sufficient that P(X|Ci)P(Ci) is the largest to guarantee the maximum P(Ci|X), for P(X) is
constant for all categories. If the priori probability of categories is unknown, let P(C1)=
P(C2)=…= P(C m) according to Bayesian hypothesis. And the maximum P(X|Ci) is only needed.
The priori probability can also be calculated by P(Ci)= Si/S, where Si is the number of training
sample in Ci , and S is the total number of training samples.
4. When there are more properties of data set, the cost of calculating P(X|Ci) is higher.
Assuming that the category condition is independent, we have
𝑝(𝑋|𝐶
𝑖) = ∏
𝑛𝑝(𝑋
𝑘|𝐶
𝑖)
𝑘=1
……….(5)
where estimated value of the probability P(X1|Ci), P(X2|Ci)…,P(Xn|Ci) can be gotten from the
training samples. If Ak is an attribute of discrete values, P(Xk|Ci)= Sik/Si . where Ci is the number of
samples and the value of Ak is Xk in Ci , while Si denotes the sample number of Ci . If Ak is a
continuous attribute, the attribute is usually assumed to obey to Gaussian distribution. Thus
𝑝(𝑋
𝑘|𝐶
𝑖) = 𝑔(𝑋
𝑘, 𝜇
𝐶𝑖, 𝜎
𝐶𝑖) =
1 √2𝜋𝜎𝐶𝑖exp [−
1 2𝜎𝐶𝑖2(𝑋
𝑘− 𝜇
𝐶𝑖)
2]
…..(6)37 where the value of sample Ak in Ci is given, g(xk,μCi,σCi) is the Gaussian density function of Ak ,
and μCi, σCi denote the mean and the standard deviation, respectively.
5. For each Ci , calculate P(X|Ci)P(Ci). The sufficient and necessary condition for assigning X
to Ci is
𝑃(𝑋|𝐶𝒊)𝑃(𝐶𝒊) > 𝑃(𝑋|𝐶𝒋)𝑃(𝐶𝒋) 1 ≤ 𝑗 ≤ 𝑚, 𝑗 ≠ 𝑖 ………..(7)
In other words, X was assigned to Ci , which maximizes P(X|Ci)P(Ci).Normal parameters values were chosen according to MICA2 sensor node standards. Experiments were done under different replay messages rates and results in [25] show that the average detection rate can reach 96% and the false detection rate 3%.
II.3.2 Misuse based IDSs
The IDS proposed in [26] relies on a modified traditional Wu–Manber (WM) pattern-matching algorithm. A string-matching (pattern-matching) algorithm is a process of searching string subsets (patterns) in a specific sentence called a text. The algorithm is used for finding words in a web page or a textbook, DNA pattern recognition, and network intrusion detection. This classical algorithm has issues of both memory efficiency and performance. A clear example is given in [27]. Suppose that the pattern is of length m. We start by comparing the last character of the pattern against tm, the mth character of the text. If there is a mismatch (and in most texts the likelihood of a
mismatch is much greater than the likelihood of a match), then we determine the rightmost occurrence of tm in the pattern and shift accordingly. For example, if tm does not appear in the
pattern at all, then we can safely shift by m characters and look next at t2m; if tm matches only the
4th character of the pattern, then we can shift by m-4, and so on. In natural language texts, shifts of size m or close to will occur most of the time, leading to a very fast algorithm.
the WM algorithm goes on the same basis using a hash table and prefix table that seeks a substring of the text to determine the shift amount. The substring, normally called a block, has two or three sequential characters [26]. These characters form the criterion for the shift amount. Referring to the hash- (i.e., the shift) table indexes, the algorithm obtains the shift amount from the table entries. Zero-shifting entries mean that the substring is a suffix of the pattern sets and have a chance to be matched with the patterns. The prefix table gives additional information about prefix subsets of the patterns to match all characters. In this way, the algorithm can skip two or more characters in the text. The skipping method enables the algorithm to find multiple patterns at once and increases the searching speed.